Access Authorization
In APIPark, subscribers subscribe to services based on applications. Each application has its own access authorization management. Once the subscription request is approved, users can use the application's access authorization information (such as API keys or tokens) to call the subscribed services. This ensures that applications adhere to security policies when calling APIs and prevents unauthorized access, ensuring the security and stability of the services.
Operation Demonstration
Configuring Access Authorization
- Select the application for which you need to configure access authorization and click to enter the inner page.
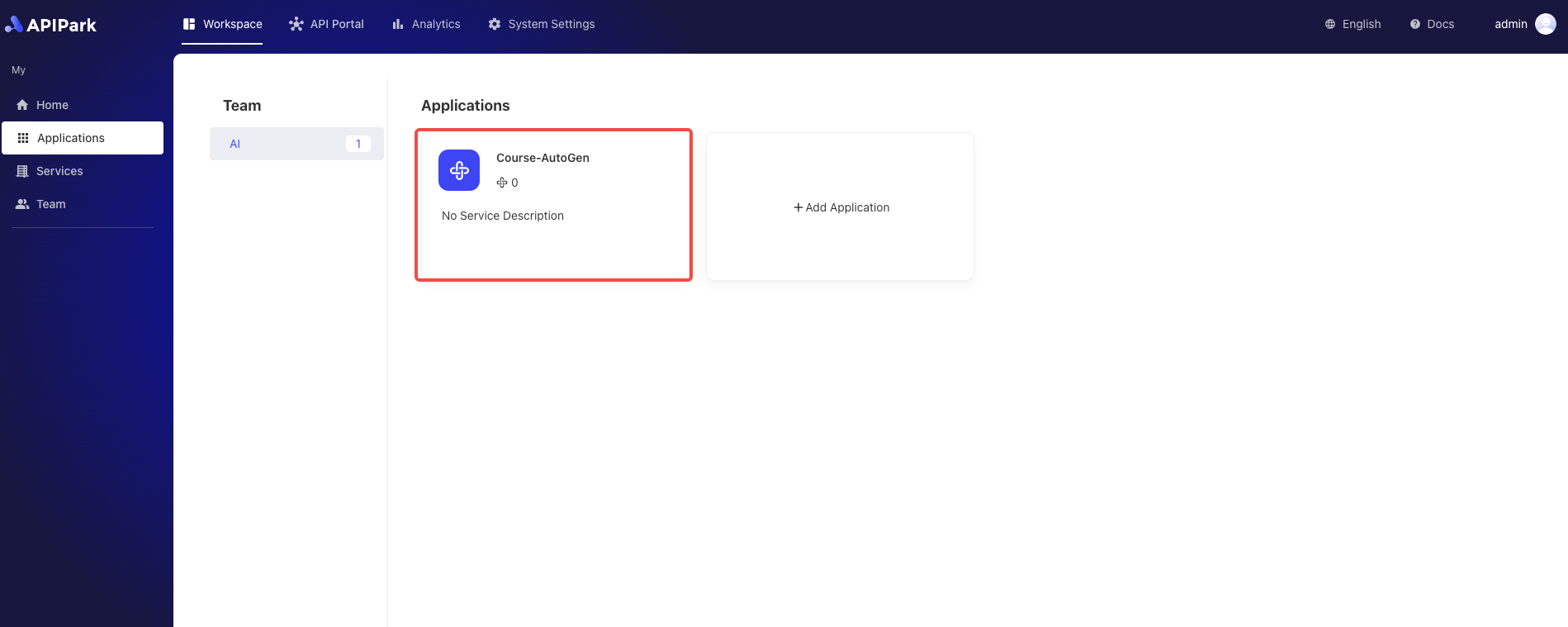
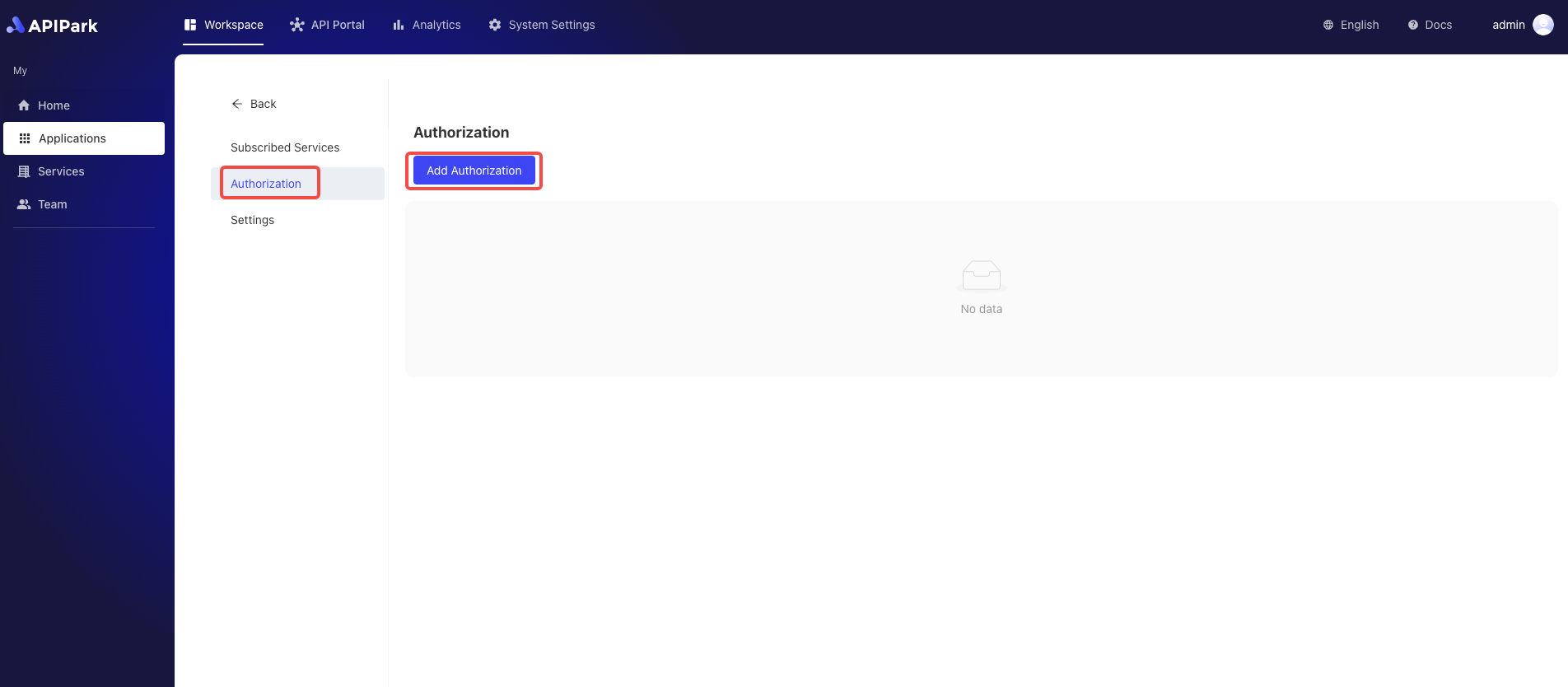
- Click
Access Authorization, enter the authorization list page, and click theAdd Authorizationbutton.
- Choose an authentication method and fill in the relevant information. Below, Basic authorization is chosen:
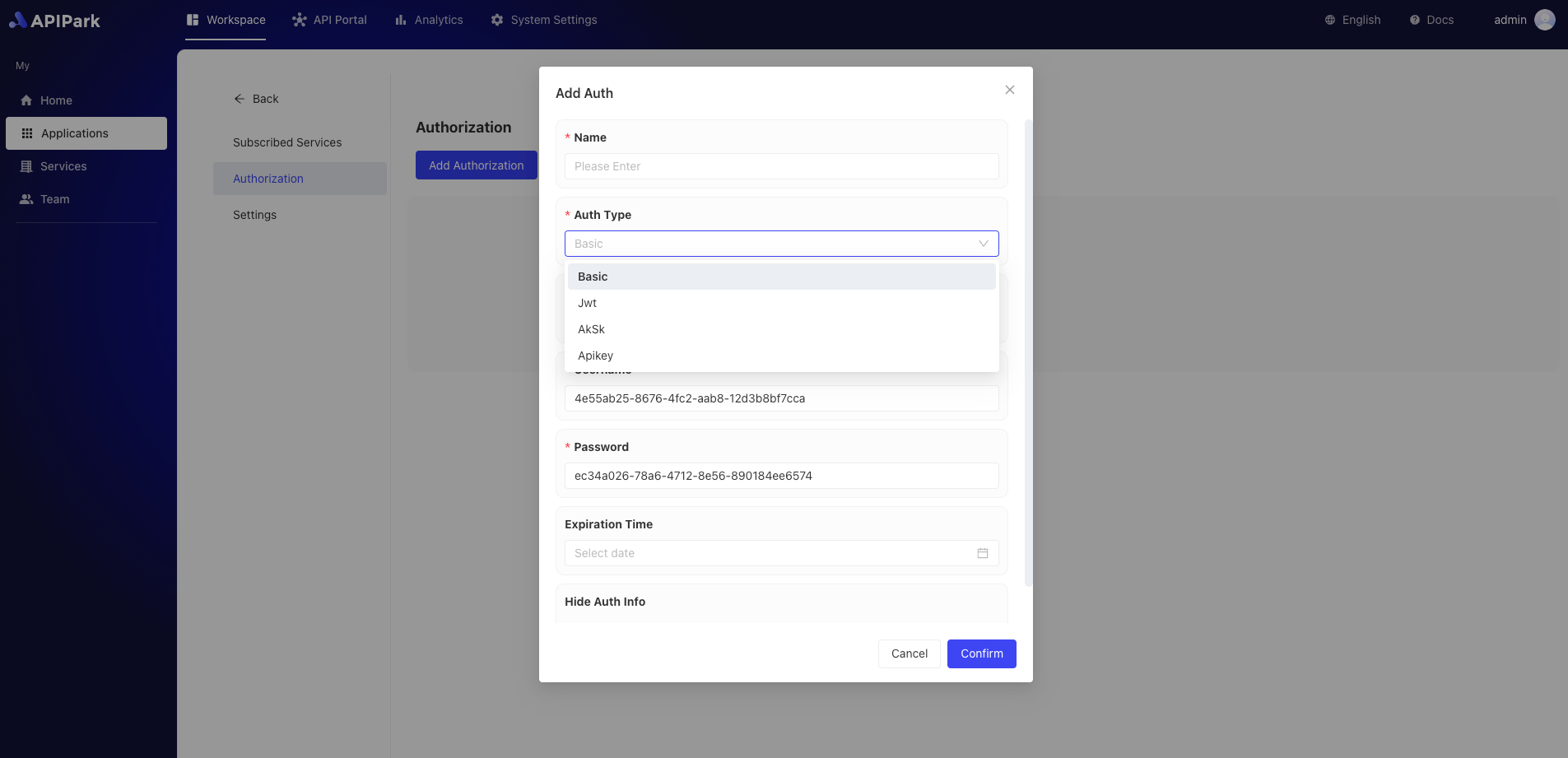
Furthermore, the platform currently supports various authentication methods such as Apikey, JWT, and AK/SK, among others.
For different types of authentication methods, the relevant common configuration fields are as follows:
| Field Name | Description |
|---|---|
| Name | Authentication identifier, it is recommended to use a meaningful name. |
| Parameter Position | The parameter position where the authentication information is transmitted, supporting Query and Header. |
| Parameter Key | Define from which key to retrieve the parameter value. |
| Expiration Time | Authentication expiration time; if not set, it will never expire. |
| Hide Authentication Information | Whether to hide the authentication fields when forwarding to upstream services. |
For more details on using authentication, you can refer to the tutorials below: